Analysis by Dikla Barda, Roman Ziakin and Oded Vanunu
Verify Level’s Risk Intel blockchain system recognized and alerted that in latest occasions, fraudsters have developed to change into more and more subtle, exploiting official blockchain protocols to conduct their scams.
The Uniswap Protocol, launched in 2018, is the most important and hottest decentralized trade for swapping cryptocurrency tokens on Ethereum and different fashionable blockchains, locking over $1.8 trillion in buying and selling quantity and 350 million swaps. Because the fifth largest software on Ethereum, Uniswap holds over $4 billion in complete worth locked (TVL) and persistently achieves billions in weekly buying and selling quantity, sustaining its place because the main decentralized trade by quantity on Ethereum mainnet, Polygon, Arbitrum, and Optimism. Secure.international in the meantime is sort of a good contract pockets and claimed to have a complete of 69million transactions, with 9.5million accounts deployed totalling $100 billion in complete belongings saved.
By leveraging the belief and performance of well-established platforms like Uniswap V3 and Secure.international, these attackers disguise their malicious actions. For example, scammers cleverly embed their assaults throughout the multicall combination perform on Uniswap V3 contract, which permits them to execute a number of transactions in a single name, thereby obfuscating their true intentions.
Equally, they make the most of the GnosisSafeProxy contract to create seemingly official contracts, that are then used to perpetrate fraudulent schemes. This crafty manipulation of trusted protocols not solely enhances the credibility of their scams but in addition makes detection and prevention considerably tougher.
The Technical Aspect of Combination Perform
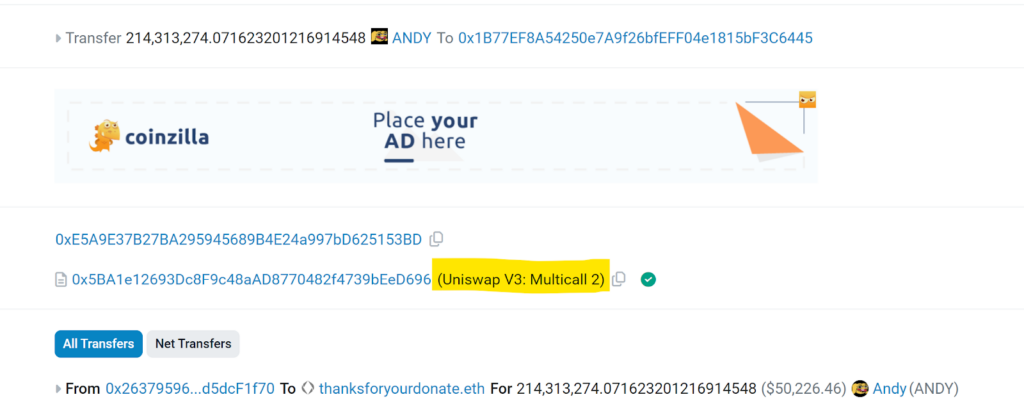
When the sufferer receives such a transaction, he’ll see that the deal with: 0x5BA1e12693Dc8F9c48aAD8770482f4739bEeD696
Needs to carry out combination, as may be seen within the following screenshot:
If the sufferer checks who this deal with is, he’ll see it’s a official Uniswap V3 Multicall2 contract.
Let’s check out the mixture perform within the multicall Uniswap contract :
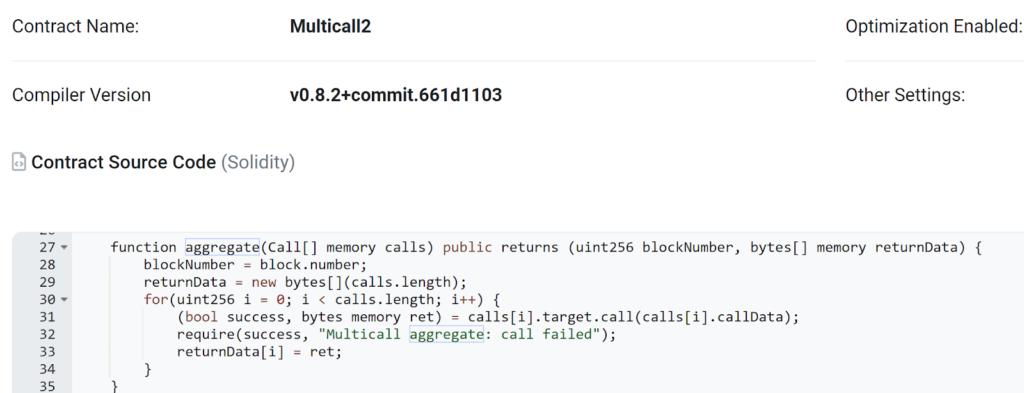
The perform takes a single parameter: ‘calls’, which is an array of Name structs. Every Name struct contains:
goal: The deal with of the contract to name.
callData: The info (perform signature and parameters) to be despatched to the goal contract.
The mixture perform iterates over every supplied name within the calls array. For every particular person name, the perform initiates a request to the required goal contract utilizing the given callData. This mechanism permits the mixture perform to execute a number of operations throughout totally different contracts in a single transaction, enhancing effectivity and transactional cohesion.
So the place is the safety concern?
The open nature of the contract, permitting any person to set targets and information parameters, poses a considerable danger. In an setting the place asset theft is rampant, the inherent belief positioned in acknowledged addresses comparable to Uniswap may be exploited. For example, if a person checks the multicall contract deal with on platforms like Etherscan, and sees that it’s labeled as related to Uniswap, they may mistakenly assume it’s protected. This perceived security may be harmful as Uniswap, being a decentralized trade (DEX), commonly interacts with person wallets for transactions.
Attackers leverage the Uniswap Multicall contract to orchestrate fund transfers from victims’ wallets to their very own. They do that by utilizing Uniswap because the spender deal with. Unsuspecting customers, seeing Uniswap listed because the spender and trusting its legitimacy, may then approve transactions they consider are commonplace operations. This approval unwittingly grants permission for the switch of their belongings straight into the attackers’ wallets.
Here’s a real-life instance illustrating how such exploitation can happen: 0xe02a450b96a2679557dc6ea214808eb0692e8b96c7a8da47f67e4e26d0086aab On this textual content, we are able to see that the Uniswap v3 multicall contract is used:
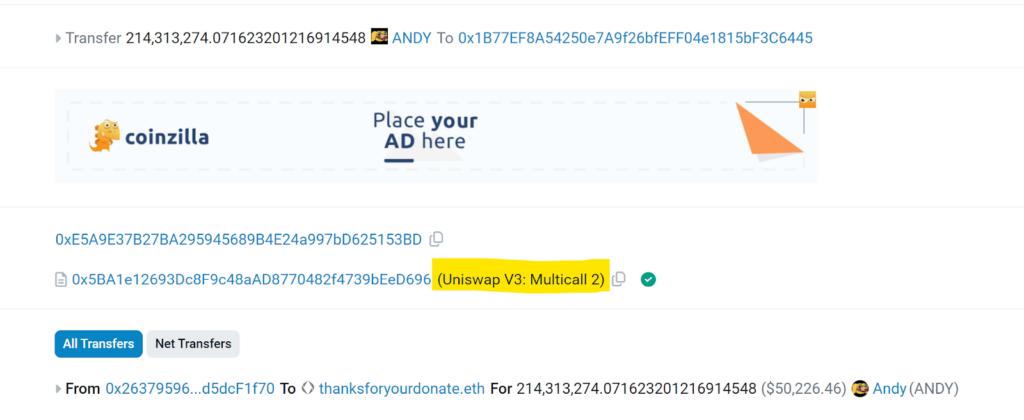
an combination perform known as:
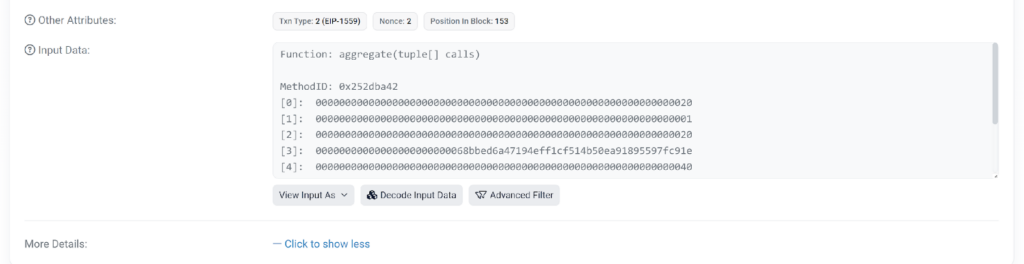
The attacker exploits the mixture perform to execute the transferFrom perform, which permits the scammer to withdraw funds on behalf of a specified pockets. To efficiently make the most of this perform, the initiator of the transferFrom transaction will need to have prior approval to withdraw cash from the focused pockets.
When inspecting the transaction logs, we observe an approval occasion. This approval was granted by the sufferer to the Uniswap Multicall contract simply moments earlier when the sufferer unknowingly signed a request, manipulated by the attacker, to extend the allowance.
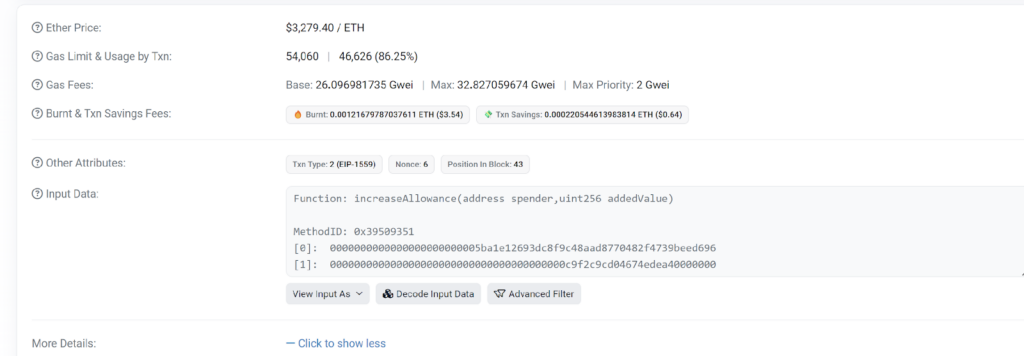
This motion successfully raised the restrict on the quantity the attacker may withdraw from the sufferer’s pockets.
Following the sufferer’s approval, the Uniswap Multicall contract was licensed to handle funds on their behalf. Leveraging this approval, the attacker initiated a transferFrom operation through the Multicall contract, which already had permission to entry the sufferer’s funds. Throughout the combination perform, the attacker-specified a goal—the precise token they supposed to steal—and used the transferFrom perform to redirect the sufferer’s cash to a pockets below their management.
Secure (previously often called Gnosis Secure) stands out as a premier selection for multi-signature wallets. This good contract platform permits customers to create and function wallets that necessitate a number of approvals to execute transactions.
To start utilizing Gnosis Secure, customers should first set up a Secure account by means of the Secure Interface. This course of assigns a novel Secure deal with to every account, linked to a Secure Proxy. The proxy is pivotal because it holds the funds and conducts transactions on behalf of the account.
Nonetheless, this infrastructure isn’t proof against misuse. Attackers have been recognized to make use of the Gnosis Secure contracts and framework, coaxing unsuspecting victims into signing off on fraudulent transactions.
An assault instance seen earlier this yr:
https://etherscan.io/tx/0x3c696c2f9af5f2717d74522c19a300cf65d2077aaf9cef435dc186 26d162a524
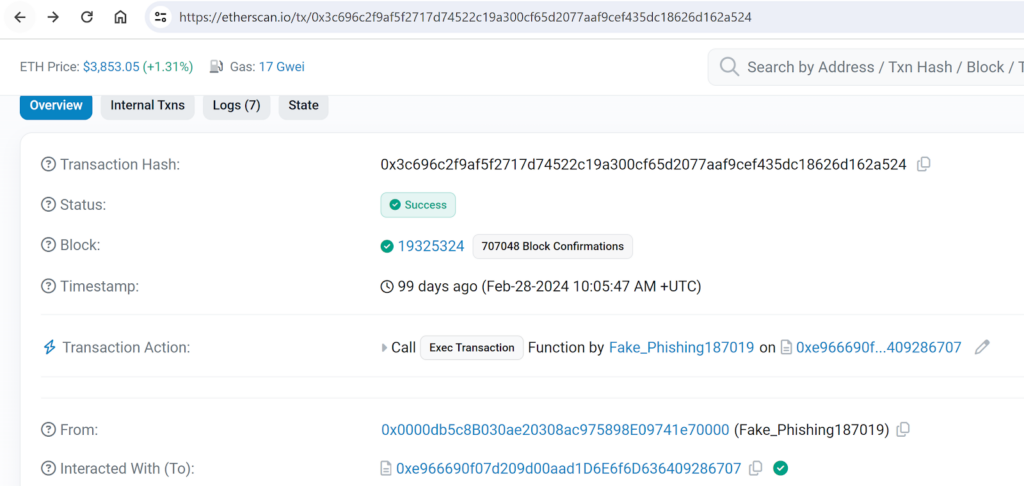
Let’s discover the way it unfolds. Initially, the attacker makes use of the Gnosis Secure framework to ascertain a official proxy contract. Subsequent, the attacker methods the sufferer into participating with this proxy contract, persuading them to hold out an “increase allowance” transaction. This motion authorizes the Gnosis Secure Proxy contract to handle tokens from the sufferer’s
pockets.
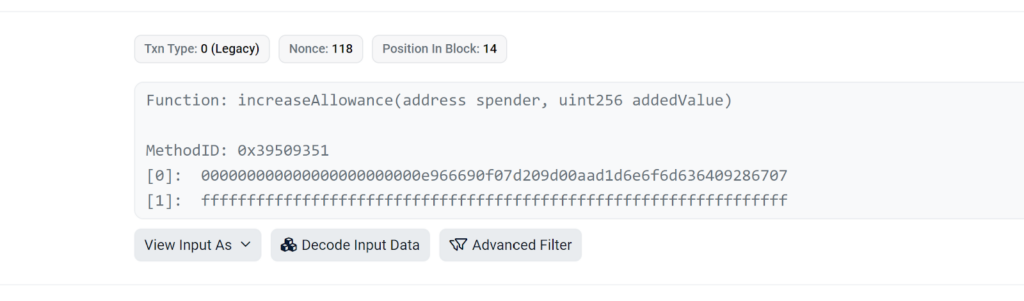
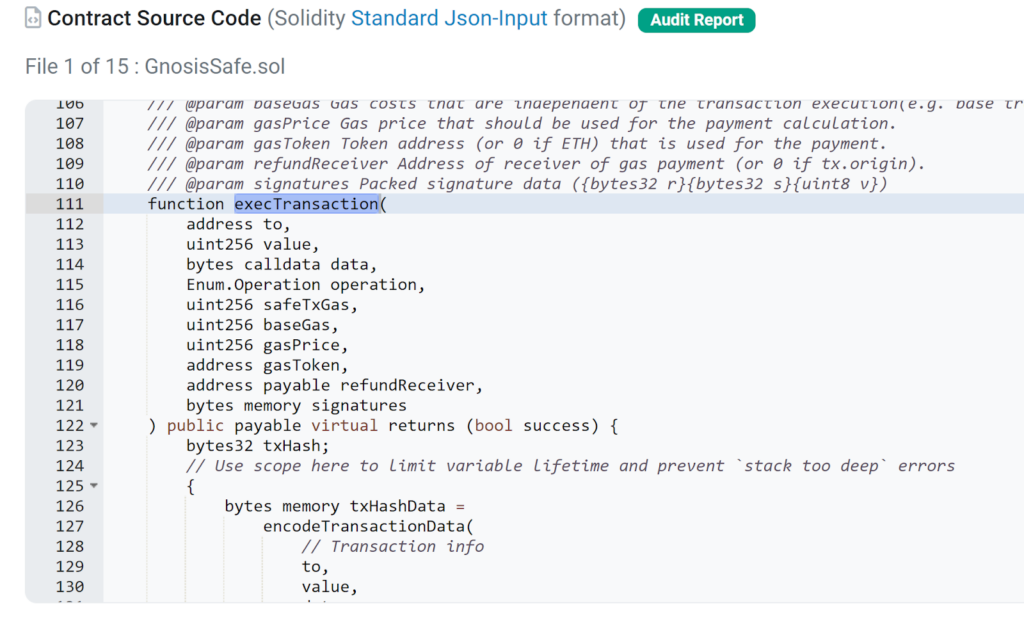
Shortly thereafter, the attacker employs the execTransaction perform on the Gnosis Secure Proxy contract to conduct a number of transactions.
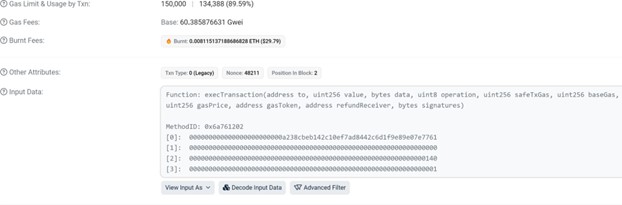
Let’s delve into how this perform operates:
When the execTransaction perform is triggered on a proxy contract, it forwards this name to the grasp copy, also called the singleton. That is achieved utilizing the delegatecall operation in Solidity, enabling the execution of the grasp copy’s code throughout the proxy’s storage
context.
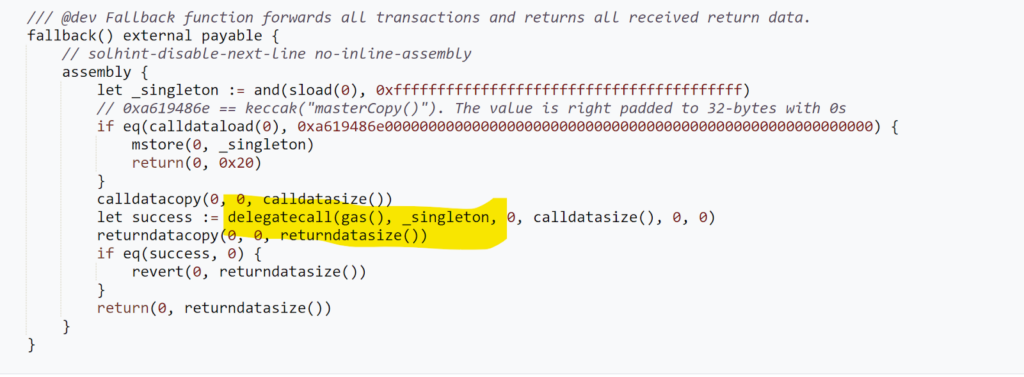
The execTransaction perform, as outlined within the singleton contract, ensures that transactions are solely executed after receiving the requisite approvals from the designated variety of homeowners, verified by means of their signatures. It additionally effectively manages fuel funds, making certain that every one transaction prices are adequately lined and refunds are issued the place mandatory. Moreover, this perform is enhanced by integration with guard contracts, which carry out further safety checks. This setup creates a safe and environment friendly framework for dealing with multi-signature
transactions.
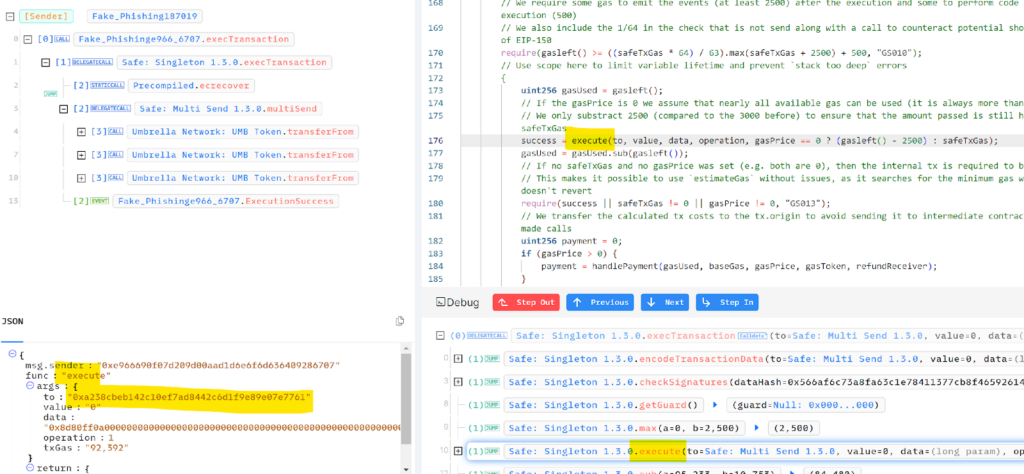
If we study the code intently, we observe that it includes a name to the Gnosis Secure Executor contract. This contract is particularly designed to facilitate transaction execution on behalf of the Secure. Inside this contract, the execute perform is triggered, which in flip calls the Secure MultiSend contract.
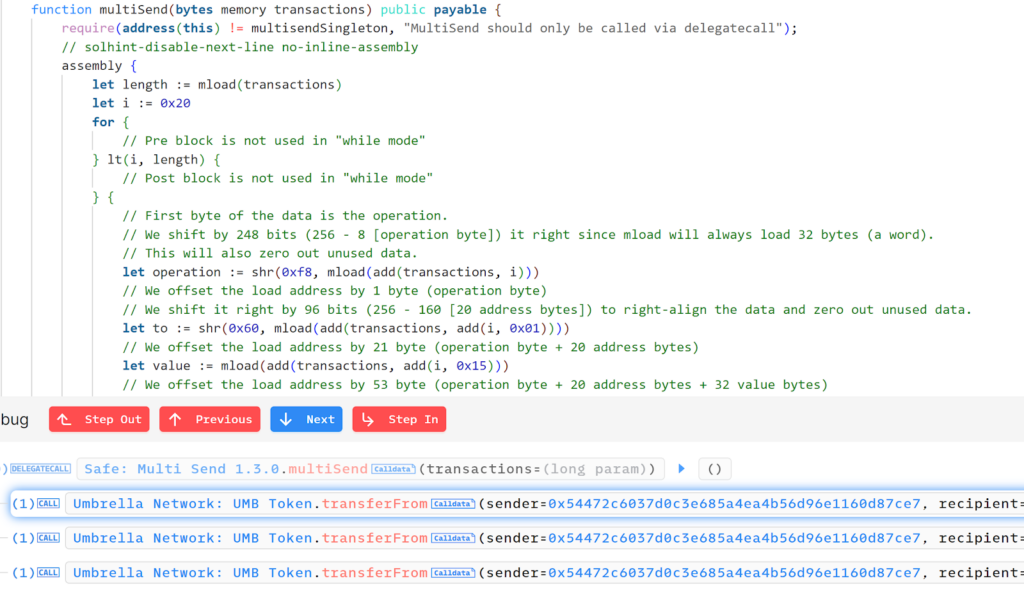
The Secure MultiSend contract is a vital element of the Gnosis Secure framework. It permits the bundling of a number of transactions right into a single operation, very similar to the mixture perform in Uniswap. This functionality is extremely helpful for enhancing effectivity and minimizing fuel prices when a number of actions have to be executed concurrently.
Analyzing the info directed to the MultiSend perform reveals that it processes three transferFrom requests involving the token “Umbrella” from the sufferer, permitting the attacker to empty the tokens from the sufferer’s pockets.
In mild of those subtle scams, it’s crucial to undertake stringent safety measures to safeguard your digital belongings.
- At all times confirm the legitimacy of contracts and their capabilities earlier than approving any transactions.
- Keep away from blindly accepting transactions, even when they seem to come back from trusted sources.
- Each time potential, carry out actions straight from the official mission web sites to make sure authenticity.
- Train warning with emails and hyperlinks on social media, as they are often vectors for scams.
- Frequently monitor your pockets and transaction historical past for any uncommon exercise.
- Keep knowledgeable concerning the newest scams and greatest practices by following respected blogs and actively participating with the blockchain group.
By implementing these proactive measures, you’ll be able to considerably scale back the chance of falling sufferer to superior fraudulent schemes.
