YEREVAN (CoinChapter.com) — Zoth protocol, a restaking protocol centered on real-world asset (RWA) publicity, skilled a significant exploit on March 21. The breach resulted in a lack of $8.4 million. The platform instantly took its web site offline and moved to upkeep mode.
Blockchain safety agency Cyvers flagged the suspicious exercise. It traced the problem to the Zoth deployer pockets, which had been compromised. The hacker drained over $8.4 million in property and shortly transformed the funds to DAI stablecoin.
The Zoth crew confirmed the hack in a public assertion. It stated the breach was a safety incident and that they’re working with companions to handle the issue. The platform additionally stated it might publish a full report after finishing the inner investigation.
Zoth Hack Funds Moved to DAI, Then Ether
Minutes after the preliminary theft, the stolen funds had been moved and transformed. In accordance with Cyvers, the attacker shortly swapped the property into DAI and transferred them to a different pockets. Later, blockchain agency PeckShield reported that the attacker swapped the DAI for Ether (ETH).
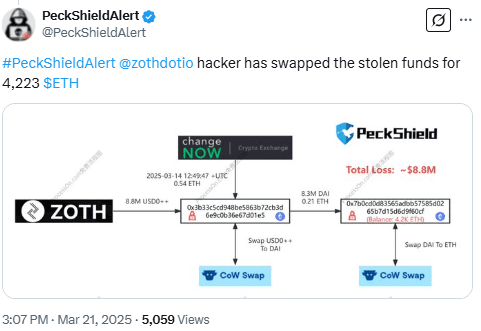
The attacker used an unlinked handle and averted centralized exchanges. The funds stay lively on the blockchain, with no replace but on their vacation spot.
Zoth protocol’s web site has not returned from upkeep. Customers don’t have any entry to providers or any up to date dashboard. There isn’t any timeline for when the platform would possibly return.
Admin Privilege Leak Triggered Zoth Protocol Breach
In accordance with Cyvers Alerts, the Zoth hack was attributable to an admin privilege leak. Hakan Unal, Senior SOC Lead on the agency, stated that about half-hour earlier than the breach, a suspicious handle upgraded considered one of Zoth’s contracts.
Subsequently, this improve changed a safe contract with a malicious model, giving the attacker management over the system.
“This method bypassed security mechanisms and gave full control over user funds instantly,” Unal instructed.
This was not a standard sort of assault. As an alternative of breaking into consumer wallets, the attacker used entry to admin-level privileges to empty property immediately from the restaking protocol.
Zoth Exploit Raises Issues Over DeFi Admin Key Dangers
Unal added that admin key compromises proceed to threaten decentralized finance platforms. He pointed to the Zoth incident for example of how attackers take management of privileged roles in good contracts.
Unal defined that instruments like multisig upgrades, timelocks, and real-time alerts can scale back danger. Nonetheless, these options weren’t in place on this case.
As of but, there is no such thing as a affirmation but on whether or not consumer funds can be recovered. Zoth protocol said it’s investigating the problem. The platform promised to launch a full report as soon as the inner evaluate is full.
