If you happen to personal any cryptocurrency, you want a protected place to maintain it as a result of crypto is among the most irretrievable belongings if misplaced or stolen. This implies having crypto wallets defined to you merely and clearly.
A crypto pockets is manner totally different from the pockets or purse you retain your typical pockets—with money and playing cards—in, it’s sometimes a software program program in your pc or an app in your cell machine. Crypto wallets retailer crypto belongings, however utilizing them correctly means conserving them and your cash protected.
On this information, you’ll study not solely what the widespread wallets are however how crypto wallets work, which sorts are finest for sure conditions, and why all of it issues. Ultimately, you’ll have a stable basis that may go a great distance towards conserving your crypto belongings protected, whether or not you’re buying and selling or HODLing.
What’s a Crypto Pockets?
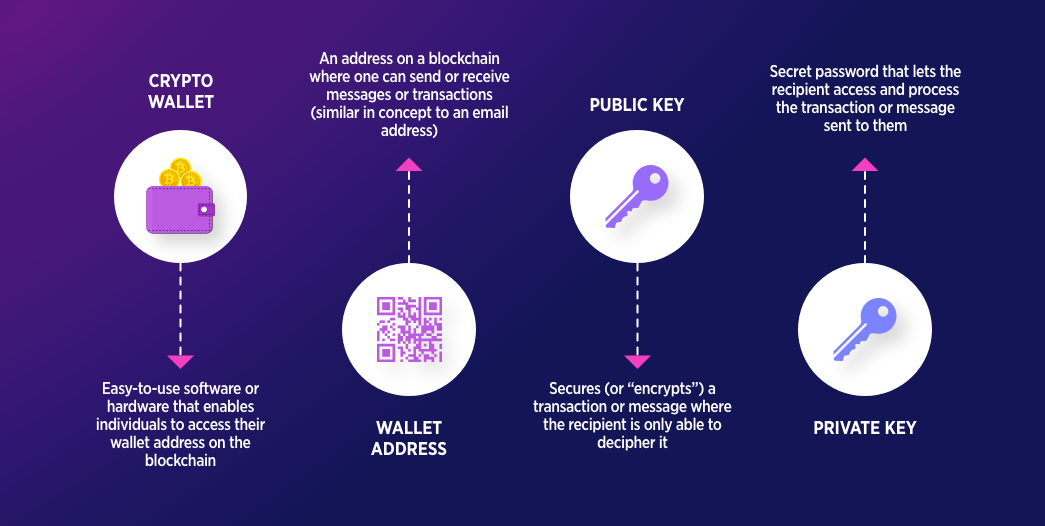
A crypto pockets is a digital interface that permits crypto house owners to handle the private and non-private keys which can be wanted to work together with blockchains. Not like conventional wallets that retailer bodily belongings, software program wallets retailer non-public keys.
Non-public keys are lengthy, advanced strings of alphanumeric characters that show possession of particular on-chain belongings. When pockets software program first creates a brand new handle, it generates a seed phrase, which is a novel phrase that can be utilized to get better the belongings should you lose entry to the precise bodily machine the place the keys are saved.
Wallets linked to the web additionally show the general public key or public handle related to a selected pockets. These addresses are the publicly seen locations on the blockchain the place cryptocurrency is shipped.
Why are Crypto Wallets Essential?
The largest factor that makes crypto wallets vital is that they provide you direct, specific management over the digital belongings saved in them with out having to depend on banks, brokers, or different third events.
While you maintain your personal non-public keys, you eradicate all counterparty danger. This implies your belongings are fully insulated from alternate hacks, account freezes, and related unexpected liquidity elimination occasions. Wallets additionally present the inspiration for permissionless dApp entry, so you possibly can lend, borrow, commerce crypto, and even mint NFTs in seconds, all by connecting your pockets to the suitable platform.
Final however not least, wallets are the idea of crypto safety measures. Chilly wallets retailer non-public keys offline in chilly storage, whereas “hot wallets” or on-line wallets safe non-public and public keys with two-factor authentication and biometric safety measures. What it comes down to is {that a} crypto pockets is the cornerstone of non-custodial wallets and the primary line of protection in your
How Do Crypto Wallets Work?
At their core, crypto wallets handle two vital items of knowledge: a public key (your pockets handle) and a personal key (your digital signature). When somebody sends you crypto, the transaction is recorded on the blockchain beneath your public handle.
To maneuver these funds elsewhere, you will need to show possession by signing the transaction along with your non-public key. Pockets software program handles this signing course of behind the scenes, broadcasting the signed transaction to the community for validation. As a result of the non-public key by no means leaves your machine, solely you possibly can authorize the motion of your belongings.
How does a crypto pockets execute transactions?
- First, you’ll have to generate the transaction by getting into the recipient’s handle and the quantity of crypto to ship in your pockets’s interface.
- Subsequent, your pockets will use your non-public key to create a signature to signal transactions by proving—mathematically—that you just personal these funds and are licensed to spend them.
- Now that the cryptocurrency transaction is prepared, it’s broadcast to the blockchain community, the place processing and validation nodes embrace it within the community.
- Notes then confirm the signature in opposition to the general public key, and supplied it’s legitimate and the pockets stability is enough, the transaction is validated and accepted onto the blockchain.
- The transaction turns into a part of the blockchain community’s ledger and is then used to verify future transactions. Most transactions usually are not thought of “complete” till they’ve a selected variety of confirmations from the community.
Completely different Kinds of Crypto Wallets
The largest distinction in crypto pockets choices is between custodial wallets and non-custodial wallets. Let’s check out what the variations are between some of these wallets after which have a look at some real-world examples.
Custodial Wallets
Custodial wallets are varied wallets managed by exchanges or fintech providers like Robinhood and Money App. Whereas they’ve an important user-friendly interface and really feel like standard on-line wallets, you might be on the mercy of the supplier’s safety. If you happen to lose entry, your pockets supplier can typically restore it.
Supply: Robinhood.com
Non-Custodial Wallets
Non-custodial wallets hold your non-public keys protected by providing you with full management over them. You generate your seed phrase, and you might be liable for conserving it saved offline. These wallets are true self-custody, and should you lose your non-public key, you can be unable to carry out any blockchain transactions.
Custodial vs. Non-Custodial Crypto Wallets: Key Variations
| Function | Custodial Wallets | Non‑Custodial Wallets |
| Key Management | Third‑celebration (alternate, service) holds keys | Person controls non-public keys |
| Restoration | The supplier can reset entry | Solely the seed phrase restores entry |
| Ease of Use | Usually easy, account‑fashion login | Requires key administration and backups |
| Danger | Counterparty danger (hacks, freezes) | Private duty; lack of keys = lack of funds |
| Preferrred For | Quick‑time period buying and selling, for learners who belief the supplier | Lengthy‑time period holding, DeFi customers, self‑sovereign possession |
Sizzling Wallets
Sizzling wallets are software program wallets which can be linked to the web.
- Desktop Wallets: Desktop PCs and laptops typically have entry to full-featured interfaces, native key storage, and even the flexibility to run a validation node. Preferrred for customers who need full on-device management.
- Cellular Wallets: Cellular wallets are widespread for Android and iOS, and these software program wallets retailer non-public and public keys for quick entry and on-the-go asset administration in a easy digital device. They sometimes have biometric or pin safety.
- Net Wallets: Net wallets are browser-based wallets or alternate account wallets which can be accessible from nearly any machine. These are the height of comfort however arguably the least safe possibility of all.
Chilly Wallets
Chilly wallets retailer your non-public keys offline, which reduces the potential assault floor to almost zero.
- Paper Pockets: Paper wallets was a handy option to reward Bitcoin wallets to folks within the early 2010s to assist it acquire recognition. They’re a printed sheet of paper with the private and non-private keys or a QR code that unlocks a pockets.
- {Hardware} Pockets: {Hardware} wallets are devoted units, just like the Ledger Nano, that each generate and securely retailer keys in a tamper-resistant chip. Transactions are signed from inside the machine, decreasing the potential for personal key breach.
How are sizzling wallets totally different from chilly wallets?
| Function | Sizzling Wallets | Chilly Wallets |
| Web Connection | On-line or steadily linked | Saved offline (air‑gapped) |
| Comfort | On the spot entry for each day use | Slower, finest for lengthy‑time period storage |
| Safety Danger | Susceptible to malware, phishing | Proof against on-line hacks; bodily theft danger |
| Typical Types | Desktop, cell, internet extensions | Paper wallets, {hardware} units |
| Preferrred For | Small to medium balances, energetic buying and selling | Massive holdings, “HODL” buyers |
Finest Cryptocurrency Wallets Comparability
| Pockets | Pockets Kind | Custody | Sizzling/Chilly Pockets | Supported Chains* | Key Options |
| Ledger Nano X | {Hardware} | Non‑custodial | Chilly | 1,000+ (BTC, ETH, SOL, and so on.) | Bluetooth, Safe Factor, staking, DeFi |
| Trezor Mannequin T | {Hardware} | Non‑custodial | Chilly | 1,000+ | Touchscreen, open‑supply firmware, Shamir backup |
| MetaMask | Software program | Non‑custodial | Sizzling | Ethereum, EVM chains | Browser/cell, DeFi swaps, {hardware}‑pockets pairing |
| Coinbase Pockets | Software program | Non‑custodial | Sizzling | Multi‑chain (ETH, SOL, and so on.) | Constructed‑in DEX, NFT gallery, ENS help |
| Belief Pockets | Software program | Non‑custodial | Sizzling | 70+ blockchains | Cellular, staking, in‑app swaps, dApp browser |
How you can Safe Your Crypto Pockets?
- Maintain your non-public keys offline, someplace protected. If you happen to don’t management the keys, you don’t management the cash.
- All the time use 2FA or MFA in your sizzling wallets and alternate accounts.
- By no means retailer seed phrases on-line. Maintain them someplace hearth and flood-safe.
- All the time use {hardware} wallets for bigger portfolios.
- Maintain a number of, redundant backups of your seed phrases in separate places.
Finest Practices for Crypto Pockets Administration
- Section Funds: Maintain a spending (sizzling) pockets for each day use and a chilly pockets for lengthy‑time period offline storage.
- Take a look at Small Transfers: Earlier than transferring giant sums, ship a small check transaction to verify the handle.
- Keep Knowledgeable: Observe pockets supplier bulletins for safety advisories or characteristic updates.
- Label Addresses: Use pockets labels or contact lists to keep away from sending funds to the incorrect account.
- Revoke Unused dApp Permissions: Periodically evaluate and revoke token approvals to restrict sensible‑contract danger.
- Monitor Exercise: Use explorers or portfolio trackers to observe for any unauthorized transactions.
- Observe Secure Looking: Phishing assaults are extremely widespread; set up anti‑phishing browser extensions and keep away from clicking on unknown hyperlinks.
- Educate Trusted Contacts: If you happen to share belongings with household or companions, guarantee they know restoration procedures.
Conclusion
Crypto wallets type the inspiration of the self-custody crypto world and provide you with true possession of your belongings. They allow you to handle your crypto holdings as you see match and with out middlement. Irrespective of which {hardware} or software program wallets you determine to make use of, make certain you’re following safety finest practices and conserving your entire units up to date and patched to assist defend your holdings long-term.
FAQs
Which crypto pockets is the most effective?
There’s nobody‑dimension‑suits‑all reply. If you happen to’re in search of peak safety, {hardware} wallets like Ledger or Trezor are going to steer the pack. For on a regular basis comfort, it’s exhausting to beat MetaMask or Coinbase Pockets, which each supply intuitive interfaces and multi‑chain help.
What’s the finest safety pockets for crypto?
{Hardware} wallets present the very best stage of safety as a result of non-public keys keep offline. Ledger Nano X and Trezor Mannequin T are business requirements for chilly storage.
Can you exchange a crypto pockets to money? How do you money out a crypto pockets?
Sure, you possibly can simply convert a crypto pockets to money. To money out, you want to switch your crypto from a private pockets to a good alternate, promote it for fiat forex, and withdraw to your checking account. Some wallets additionally combine on‑ramp/off‑ramp providers for direct money‑outs.
How you can use a crypto pockets?
Obtain or set up the pockets, securely retailer your seed phrase, fund the pockets by receiving crypto to your public handle, and signal transactions along with your non-public key to ship or work together with dApps.
Is a crypto pockets protected?
A pockets is as protected as its safety practices. Non‑custodial wallets hold management in your arms, however you will need to safeguard the keys. {Hardware} wallets and powerful operational safety drastically scale back danger, whereas poor key administration can result in loss.
