YEREVAN (CoinChapter.com) — North Korean-affiliated hacking collective Lazarus Group continues laundering stolen cryptocurrency whereas increasing its malware operations. On March 13, blockchain safety agency CertiK recognized a 400 ETH ($750,000) deposit into Twister Money, a crypto mixer identified for obscuring transaction histories.
CertiK linked the funds to Lazarus Group’s actions on the Bitcoin community. The group has been behind a number of high-profile trade hacks, together with the $1.4 billion Bybit hack on Feb. 21 and the $29 million Phemex breach in January.
These newest transfers add to Lazarus’s historical past of laundering stolen belongings. In 2022, the group orchestrated the $600 million Ronin community hack, one of many largest DeFi exploits ever recorded. In line with Chainalysis, North Korean hackers stole $1.3 billion in 2024 throughout 47 incidents, greater than double the quantity stolen in 2023.
New Lazarus Malware Targets Crypto Builders
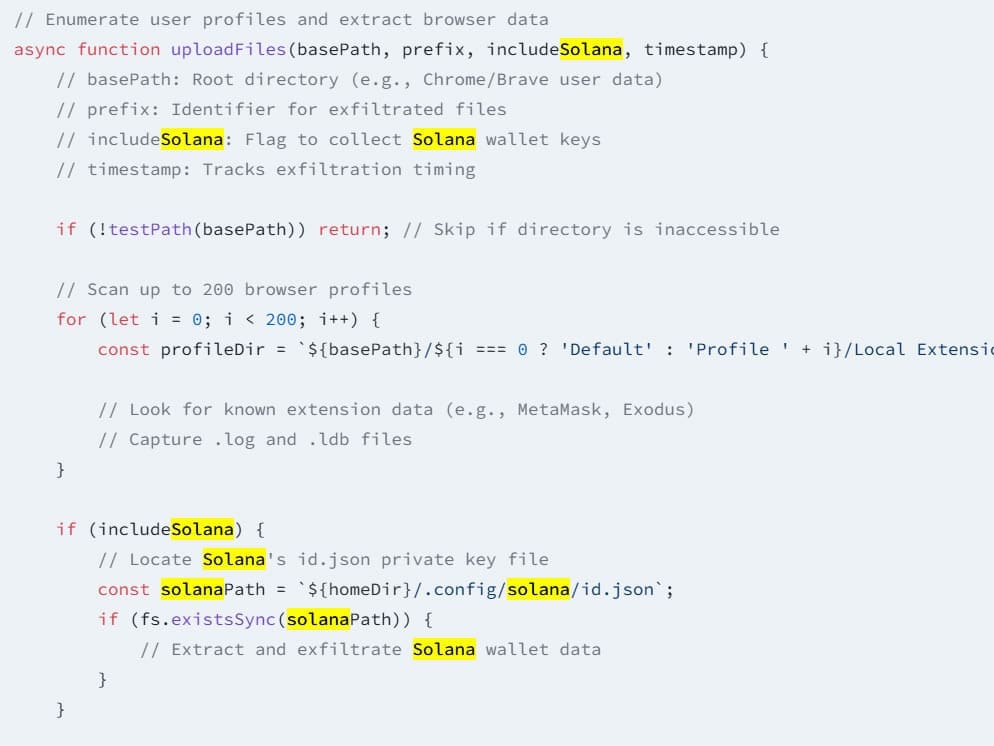
Cybersecurity researchers at Socket detected six new malicious packages deployed by Lazarus Group. These packages infiltrate developer environments, steal credentials, extract cryptocurrency knowledge, and set up backdoors.
The malware primarily targets the Node Package deal Supervisor (NPM) ecosystem, which hosts JavaScript libraries extensively utilized by builders. Researchers discovered a pressure known as “BeaverTail” embedded in packages that intently mimic professional software program libraries.
“Across these packages, Lazarus uses names that closely mimic legitimate and widely trusted libraries,”
Socket researchers famous. The group makes use of typosquatting ways to deceive builders into putting in malware.
Lazarus Group’s Malware Targets Crypto Wallets
The brand new malware particularly assaults cryptocurrency wallets, together with Solana and Exodus wallets. It additionally scans for delicate information saved in Google Chrome, Courageous, and Firefox browsers, aiming to extract non-public keys and credentials.
On macOS, the malware targets keychain knowledge, posing a big menace to builders who unknowingly set up these compromised packages. The malicious code grants attackers entry to encrypted credentials, permitting them to steal funds straight.
Whereas researchers haven’t definitively attributed the assault to Lazarus Group, they famous that the strategies used on this NPM assault intently align with Lazarus’s identified operations.
Lazarus Group’s Historical past of Crypto Crimes
Lazarus Group stays a dominant participant in crypto-related cybercrime. The collective has been concerned in a number of the largest hacks in historical past, specializing in crypto exchanges, DeFi platforms, and developer environments.
The group’s newest exercise highlights an ongoing effort to each launder stolen belongings and increase malware campaigns. Above all, this places builders and crypto customers at continued danger.
